Choose the right plan for your developers
-
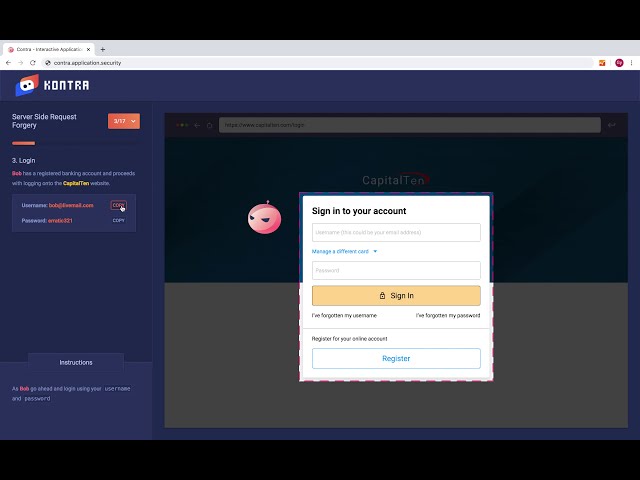
- For Teams with 5-15 Developers -
Squad
The ultimate package for your
tight-knit squad
-
Premium Course Access
-
Full Premium Access
-
Languages & Frameworks
-
Full Premium Access
-
SSO/SAML/AD Integration
-
-
API Endpoints
-
-
Full Industry Compliant Training(OWASP TOP 10/HIPPA/PCI DSS/ISO27001/SOC2)
-
-
Full Compliance Reporting Capabilities
-
-
SCORM Compliant Content
-
-
Enterprise Volume Discount
-
-
- Starting from 16 Developers -
Brigade
For the brigades who never
stop growing
-
Languages & Frameworks
-
Full Premium Access
-
SSO/SAML/AD Integration
-
-
API Endpoints
-
-
Full Industry Compliant Training(OWASP TOP 10/HIPPA/PCI DSS/ISO27001/SOC2)
-
-
Full Compliance Reporting Capabilities
-
-
SCORM Compliant Content
-
-
Enterprise Volume Discount
-
|
- For Teams with 5-15 Developers - |
- Starting from 16 Developers - |
|
Squad |
Brigade |
|
|
The ultimate package for your
tight-knit squad
|
For the brigades who never
stop growing
|
|
 |
 |
|
|
Premium Course Access |
Full Premium Access |
Full Premium Access |
|
Languages & Frameworks |
Full Premium Access |
Full Premium Access |
|
SSO/SAML/AD Integration |

|

|
|
API Endpoints |

|

|
|
Full Industry Compliant Training
(OWASP TOP 10/HIPPA/PCI DSS/ISO27001/SOC2)
|

|

|
|
Full Compliance Reporting
Capabilities
|

|

|
|
SCORM Compliant Content |

|

|
|
Enterprise Volume Discount |

|

|
Trusted by leading companies around the world
Frequently Asked Questions
For example, a SQL Injection vulnerability cannot be categorized as easy, medium, or hard since the vulnerability is a high-risk issue, and therefore regardless of a developer's experience and seniority, every software developer in an organization must know what this issue means and how it impacts the security of your application.
However, we do categorize courses by roles and job functions. See the next question.
- Frontend Developers: These are developers who focus on UI/UX development
-
Backend Developers: These are developers who focus on developing the backend business
logic and functionality of the platform. -
Database Developers: These are developers who focus on developing the backend business
logic and functionality of the platform.
Our content is further used by system architects to educate them on the common attack surfaces present during the design stage of an application.
- Java
- .NET
- Ruby on Rails
- Python(Django)
- Python(Flask)
- Scala
- Kotlin
- Node.js
- GO
- PHP
- Angular
- React
- Vue.js
- Course Start Database
- Total Time Spent
- Total Progress in %
- Last Login Time
- Total Time spent on every course
- Total Time spent on primary course
- Total Time spent on every exercise
- Number of times an exercise was attempted
- Certificate of Completion(PDF)
- Single Users
- Multiple Users
- Send reminders based on % of completion i.e. Send reminders to all users that have only completed 20% of their primary course etc.
- Improvements in the existing content library
- New courses on topics
- New exercies for existing courses
However, unlike our competitors we are not aiming to stuff our platform with repetitive content, a practice known as “content stuffing” - Developers can sense and pick this up very quickly and will not engage with the training if the content is simply updated for the sake of it.
- PCI (Payment Card Industry) compliance requirements.
- HIPAA
- SOC2
- ISO27001
Some leading learning management systems that Kontra customers use today:
- Workday
- Articulate Rise
- Docebo
- CornerStone
- Lessonly
- SkillSoft
- Saba
- SAP SuccessFactors
- Moodle
- Okta
- Google Apps
- Ping Indentity
- Azure AD
- Microsoft AD
- SailPoint
- OneLogin
- Auth0
Ready to get started?
Experience the full Kontra platform
and see what it can do for you and your team.