Kontra OWASP Top 10 for Web
KONTRA's developer security training of OWASP Top 10 is inspired by real-world vulnerabilities and case studies, we have created a series of interactive application security training modules to help developers understand, identify and mitigate security vulnerabilities in their applications.
-
Clickjacking

-
Command Injection

-
Components with Known Vulnerabilities

-
Cross Site Request Forgery

-
Directory Traversal

-
DOM XSS

-
Forced Browsing

-
Header Injection

-
Horizontal Privilege Escalation

-
Insecure URL Redirect

-
Leftover Debug Code

-
Log4j 2 CVE-2021-44228
NEW
-
PII data in URL

-
Reflected XSS

-
Ruby rest-client 1.6.13 backdoor vulnerability

-
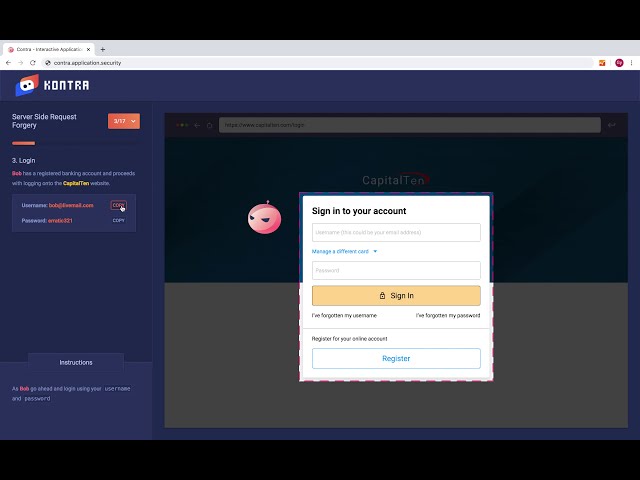
Server Side Request Forgery

-
Session Fixation

-
SQL Injection

-
Stored Cross Site Scripting

-
TikTok Cross Site Scripting Vulnerability

-
Token Exposure in URL

-
User Enumeration

-
Vertical Privilege Escalation

-
Weak Randomness

-
XML Injection