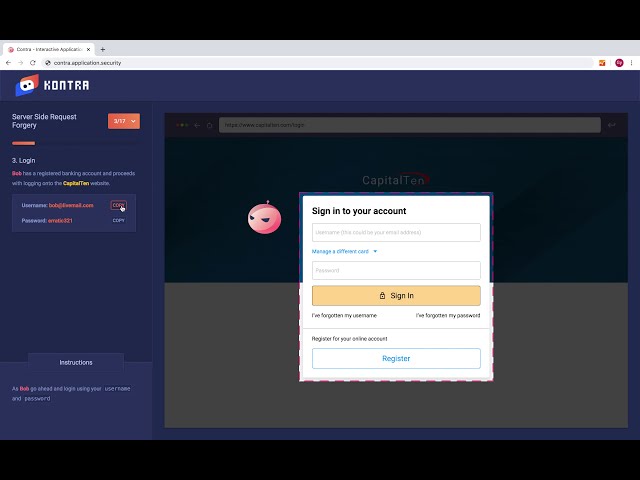
Kontra Docker Compose Top 10
Learn common security threats & vulnerabilities encountered and detailed best practices for Docker Compose.
-
Container Resources Limitation
NEW
-
Exposed Docker Socket
NEW
-
Host Update
NEW
-
Improper Write Permissions for Volumes and Host Filesystem
NEW
-
Insecure Container Registries
NEW
-
Minimal Base Image
NEW
-
Privileged Containers
NEW
-
Sensitive Data Leak via Docker Images
NEW
-
Unsegregated Container Network
NEW
-
Unverified Container Images
NEW